Cyber Risk: A Perfect Storm Approaching Europe?

Technicians work on a protective cybersecurity system on January 24, 2017 in Lille, France, during the International Cybersecurity Forum.
Photo: Philippe Huguen/AFP/Getty Images
A perfect storm of cyber threats is bearing down on the European Union in the form of increased infrastructure attacks, sweeping new regulations, and businesses fundamentally unprepared for these changes. Put simply, Europe’s cyber threat landscape is about to change dramatically.
The first major trend is the evolution of cyber risk from digital to physical assets. While the loss of personal financial and health records is disturbing, the spectre of cyberattacks against critical infrastructure is the new reality in Europe. The trend began in late 2014 with a crippling cyberattack against a German iron plant and accelerated in 2015 when hackers disabled power utilities in the Ukraine.
In response to these developments, companies and governments throughout Europe need to prepare for the possibility that future attacks will be measured not just in reputational damage but also in large-scale property damage; not just in dollars, but also in lives lost.
New vectors of attack are being launched, too. Following the U.S. presidential election, we must, for the first time, include political parties and voting apparatus as part of this critical infrastructure. With major national elections taking place in the coming months in the Netherlands, France and Germany, the risk of attacks aimed at destabilizing governmental institutions is a sobering reality.
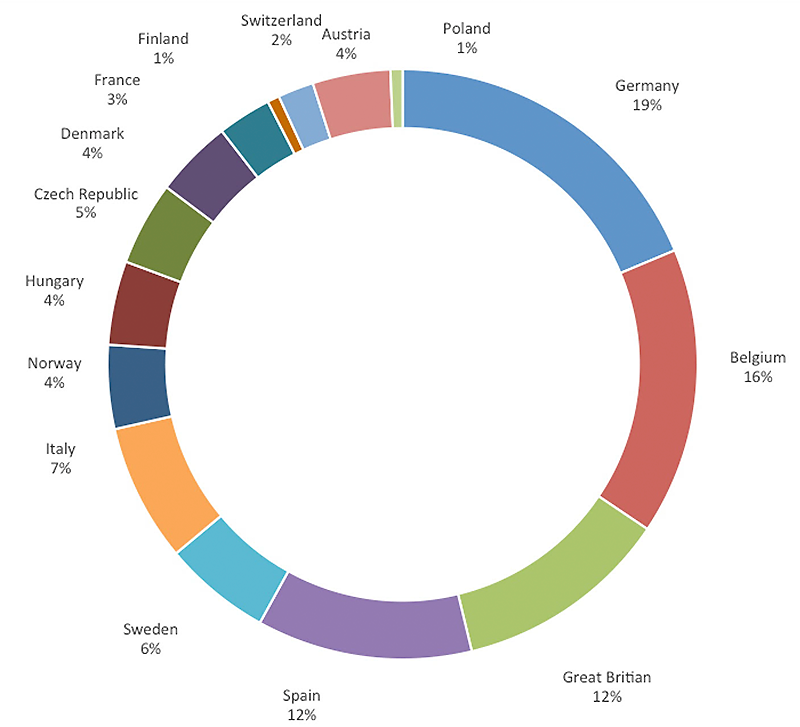
Europe’s largest economies remain the top targets for cyber attacks, but the focus ranges broadly across the continent. This figure shows targeted malware detections in Q1 and Q2 2016 for 10 EU nations. (Nations not represented on this chart received little or no malware assessments from FireEye.) Source: FireEye
Awareness of cybersecurity as a major threat in Europe is at an all-time high. This is an important first step. But one of the greatest challenges throughout the EU today is getting beyond awareness of the problem and moving toward specific, actionable understanding of the dangers ahead. The saying “you don’t know what you don’t know” holds particular truth for cybersecurity, where a lack of awareness will have major consequences.
As a leading indicator of the challenge, FireEye determined that organizations across Europe take three times longer to identify cyber intrusions than the rest of the world. The time between compromise and discovery, known as “dwell time,” was 469 days in the EU versus a global average of 146 days. This longer dwell time gives intruders ample time to get inside a network, root around for data of interest, move laterally within IT environments and develop multiple entry points and back doors.
One critical reason for this longer dwell time is Europe’s less stringent reporting requirements, which have limited the obligations of European companies to disclose publicly the volume, scope and details of significant cyber breaches. But that’s about to change dramatically.
Regulation Leads to Accountability
The EU’s adoption of the sweeping General Data Protection Regulation (GDPR) will soon require companies across the continent to publicly disclose data breaches to national protection authorities and, where the threat of harm is substantial, to affected individuals. The Rapporteur assigned by the European Parliament to lead the final GDPR negotiations, Jan Albrecht, announced upon its passage in the summer of 2016: “The GDPR will change not only the European Data protection laws but nothing less than the whole world as we know it.”
When GDPR goes into effect in next year, companies will change how they retain and use an individual’s personal data, and will be held to far stricter accountability and sanctions regarding security breach notification, data privacy and data protection. Its implications will be immense. On January 1, 2016, Dutch authorities implemented a “mini-GDPR,” which resulted in more than 5,500 cyber incident reports in one year alone. Extrapolating these figures across the EU, it’s easy to see how profound the coming changes will be.
Though the GDPR does not take effect until early 2018, now is the time to prepare. When cyber breaches begin to fill the headlines of major European newspapers, management teams will be pressed as never before to address concerns from data protection authorities, supervisory boards and journalists about their state of preparedness. With that in mind, these steps are critical:
Cybersecurity is not solely an IT issue. The most senior members of a company’s management team must engage and be at least conversant with this dynamic risk. In your organization, can the CEO, the CFO or the GC answer the following three questions:
- What are your company’s principal cyber vulnerabilities?
- What are your key strategies for mitigating those risks?
- Are adequate resources being devoted to the task at hand?
Vulnerability assessments are essential. Every company should conduct a vulnerability assessment. The best place to start in 2017 is to benchmark your cyber protocols against an established standard. What are your most critical cyber assets? Does your organization primarily rely upon proprietary data or industrial control systems? Have you assessed the true financial consequences of a large-scale breach?
Cyber risk is now a board-level issue. Supervisory boards in Europe will be putting far more focus and pressure on management teams in the coming year. Expect your board to ask questions about patching software vulnerabilities, implementing multifactor authentication for user access, and conducting risk assessments of third-party vendors and suppliers. If it takes your organization three times longer to identify a cyber intrusion as other companies, will that be satisfactory for your board?
Corporations should engage with external stakeholders. If the premise is correct that cyber breaches will become a far more public issue for European corporations in the coming 12-18 months, now is the time to prepare by reaching out to build relationships of trust with data protection and law enforcement authorities, policymakers and the press. In addition, have you engaged top-notch security experts to respond to an incident?
Governments in Europe must lend a hand to the business community. Given the particular threat posed to critical infrastructure, governments in Europe should reach out more affirmatively to the business community on two fronts:
- By sharing threat intelligence in real time regarding the latest forms of attack and known malicious IP addresses.
- By promptly alerting businesses that their systems have been breached. An enhanced level of trust between government and industry will pay dividends in a host of different areas.
It is not easy for a corporate executive to admit a lack of preparedness on any issue, but on cybersecurity, the stakes are too high. Now is the time for every company to take a hard and critical look at its policies and procedures and get ready for the rocky road ahead.







