Fighting for Cyber Talent in a Competitive Market

A student from a Paris engineering school attends the first edition of the Steria Hacking Challenge.
Photo: Thomas Samson/AFP/Getty Images
Organizations face three challenges related to cyber talent: Who is responsible for risk mitigation today? What skills are corporations seeking to staff their growing talent needs? And what steps are employers taking to keep the talent they have today?
Given the dearth of graduates from accredited cybersecurity programs—and the growing desire for personnel with related education, experience and certification—talent to fill open positions is scarce.
Companies may find themselves well-served in providing current cybersecurity staff with the education to achieve certified status, and then compensating them well enough to retain their newly trained talent from competitive offers.
Given the enormity of the potential risk and its impact on lost business (Lloyds of London estimated that cyber attacks are costing businesses $400 billion annually), far too many companies are strangely complacent. Only slightly more than half (53 percent) of the respondents in a 2016 Mercer Select Intelligence global survey reported that their organizations viewed cybersecurity as imperative across the entire organization. While the majority of respondents felt that they were organized to meet the tasks and challenges ahead—and were already sourced to build a flexible staffing model with the right mix of staff, consultants and contractors—far fewer (47 percent) felt they were adequately staffed in terms of talent to meet tomorrow’s challenges.
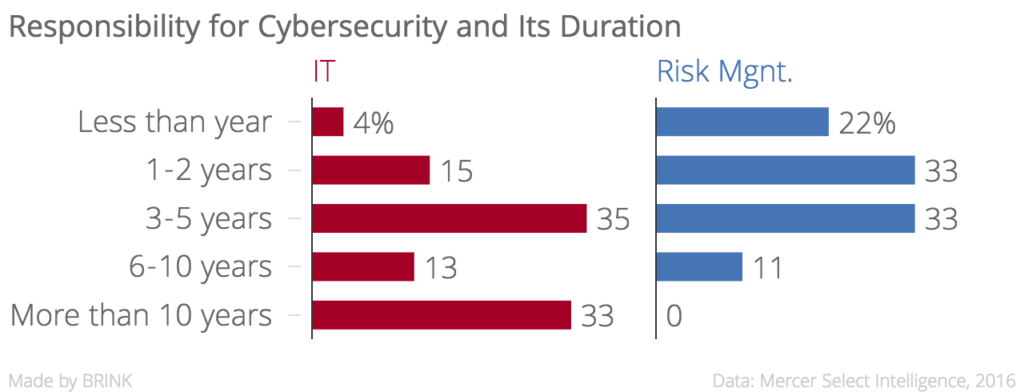
Who Owns Cyber Risk Mitigation?
Traditionally, responsibility for computer-related security rested in the IT department, especially for those companies that have maintained a designated cybersecurity function for more than 10 years. For many organizations, we see a shift to departments of risk management for cyber responsibility. While this is a growing trend and development, it is less than five years old. (See chart below.) This may speak to one of several tendencies:
- An increase in organizational functions specific to risk management
- A growing trend to house cybersecurity within the overall corporate strategic risk function rather than in IT
- The growing focus of cyber risk management as a C-suite strategic risk issue
Interestingly, 21 percent of those responding organizations in which cybersecurity responsibility is housed in the IT function viewed it as a crucial priority inside IT, but not as a priority within the business units or at higher levels of management. This contrasts significantly with those organizations that housed cybersecurity within a risk management department, for which not one respondent thought that cyber concerns were limited to his or her department. This finding showcases the overall shift in perspectives on cyber attacks as a strategic risk management function rather than solely an IT charter.
Staffing Cybersecurity Initiatives in the Face of Talent Scarcity
The majority of companies (86 percent) indicated intent to increase spending on cybersecurity staffing within the next 12 months. Given the noted scarcity of cyber professionals, competition for talent is increasingly intense. Finding talent, training current employees and retaining trained talent loom as major issues in this critical mission. The vast majority of companies surveyed plan to increase the size of their cybersecurity teams over the course of the next two years, with 25 percent of those actively recruiting full-time employees today and another 25 percent actively recruiting part-time employees or are contingent on external vendors for support. While some organizations have no intent to expand (26 percent), none expect to contract.
Cybersecurity Qualifications Sought by Employers
Qualifications for cyber-risk mitigation professionals and even initial entrants into related positions are stringent, with higher levels of education, experience and certifications sought, whether the positions reside in a risk management division or within an IT department.
Education
Education varies with the position sought, with the majority requiring college graduates and top positions requiring advanced degrees. Between 60 and 73 percent of respondents require a bachelor’s degree for all jobs and one-third of companies require a master’s degree for C-Suite positions (CISO, CSO, CTO, CIO).
Experience
Even entry-level positions are requiring several years of experience. Almost half of employers looking for cyber engineers, for example, require more than three years of related experience. Analysts appear to be better able to enter the job force with one to two years of experience, though a quarter of respondents sought more than three years of experience for such positions.
Security Certification
As risk management and IT positions increase, so does the desire for certified professionals across a variety of cybersecurity job types. Some employers prefer multiple certifications for some positions; no positions for which employers are hiring require none at all. The Certified Information Systems Security Professional credential is the most generally sought certification over the widest range of positions.
The Challenge: Finding Talent with Desired Qualifications
Given the extent of requirements for open positions, predictably, these jobs are hard to fill. Almost one-half of respondents reported that filling cybersecurity positions was difficult or very difficult, and none responded that it was very easy.
Degrees of difficulty are, of course, dependent on the position and the level of qualifications: education, experience and valid certifications sought. Analyst positions appear to be more difficult to fill than engineers with cyber or security experience. Employers cite different reasons—external and internal—for this difficulty. The foremost reasons are the lack of experience and education in the market to fulfill cybersecurity roles, especially at senior levels. Half of the respondents, however, view an internal failure to compensate such talent at the market rate as the main reason they cannot attract the staff they need.
Time to fill cyber positions is often protracted: 23 percent of respondents reported they exceeded 120 days to fill positions at the C-Suite or director level. One-fifth (21 percent) reported that they target the 75-plus market data percentile for base salary when recruiting for these cybersecurity positions. Filling a role as an analyst of information security, security operations, risk/vulnerability or network security took between 61 and 90 days for 16 percent of respondents.
While the slight majority of companies do not treat security candidates any differently in the recruiting processes, some are offering incentives to try to lure this specialized population. Flexible schedules, location choices, hiring bonuses and higher base salaries are the predominant methods used to attract candidates.
Keeping Existing Cyber Talent
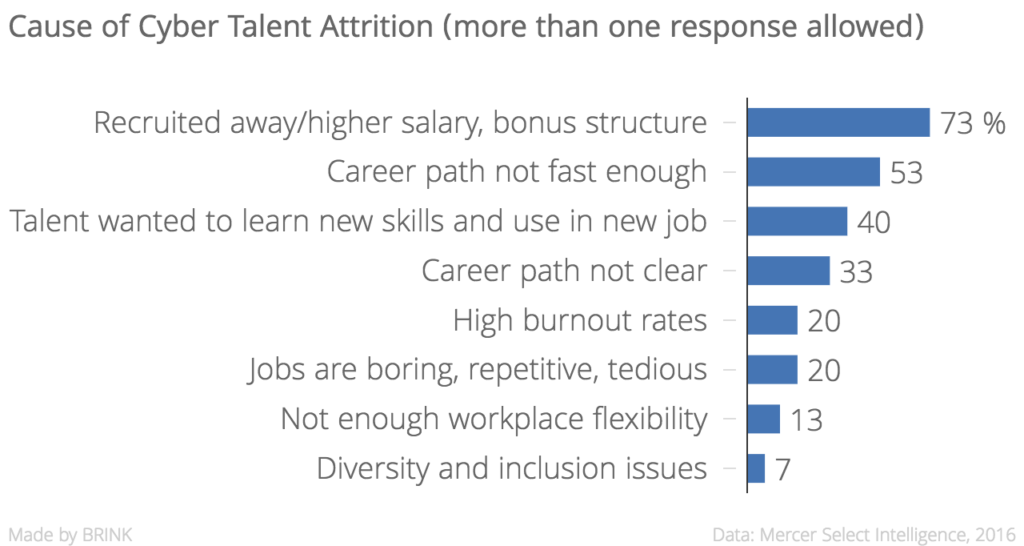
Most of the companies in our survey had an internal cyber pool; while they were seeking additional talent, they were worried about keeping the talent they already had. Twenty-seven percent reported it was difficult to do so; only 15 percent thought it was relatively easy. Retention issues stem from two highly sought after positions: security auditor and the analyst of information security, security operations, risk/vulnerability or network security. Both positions were identified by 23 percent of companies as the hardest to retain.
The primary reason for the loss of cyber talent was the lure of higher salaries elsewhere, as perceived by 73 percent of respondents. Concern for career-relevant skills and lack of a fast career path were the next elements that led to employee loss to competitors.
Given this, the majority address the desire for training as a primary lure for retention. Many do nothing, similar to those who do nothing to attract candidates to their corporations. Combinations of flexible time and various bonus types are also used as retention devices.
Creating a sound basis for organizational cybersecurity starts from the top, but it does not end there. Based on our research, the standard HR issues of sourcing, hiring, grooming and retaining qualified staff clearly come into play.
Maintaining a cyber risk-mitigation environment is a race without a finish line—it is a threat that is not going to go away.