2017: The Shifting Cyber Threat Landscape in Asia-Pacific

A man uses a computer in an internet cafe in Beijing in June 2017. In Asia-Pacific, cyberattacks with financial motivations are perceived as a top threat for international corporations across industry sectors.
Photo: Greg Baker/AFP/Getty Images
2017 saw an unprecedented wave of cyberattacks, accompanied by an alarming rate of cybersecurity meltdowns. The wave of global ransomware attacks last year has forced a hard reflection on how governments, businesses, and individuals can protect themselves from this threat in the future.
The cyber threat landscape morphed dramatically in 2017, and the indications are that it will continue to evolve. Cybercriminals and other threat actors with malicious intent are now more sophisticated than ever, finding new and inventive ways to carry out attacks. The Asia-Pacific region is no different, as illustrated in a new report by FireEye and Marsh McLennan Companies.
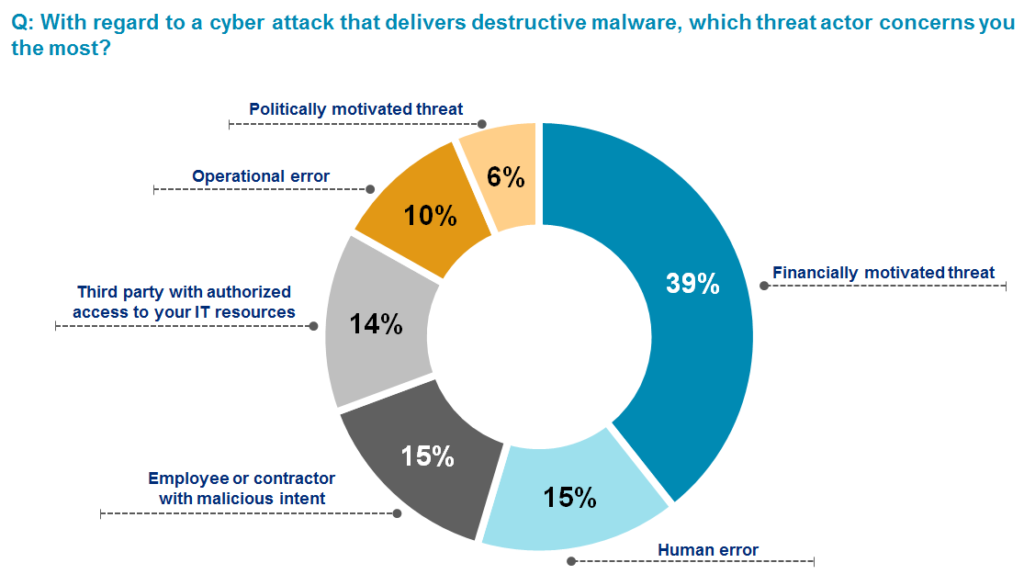
According to a survey conducted by Marsh and Microsoft in July and August 2017, cyberattacks with financial motivations (39 percent) were perceived as the top cyber threat for international corporations across industry sectors in APAC (Exhibit 1). Extortion for financial gain has become the key goal of stealing insider information and/or confidential intellectual property, making it reasonable to expect that inventive techniques will continue to emerge and evolve in the cyber risk landscape.
Exhibit 1: Survey of corporations’ views on the top cyber threats when doing business across Asia-Pacific
At the Crossroads of Emerging Technologies and Cyber Risks
The growing interconnectedness between both digital and physical worlds and the increasing dependence on information technology systems have exponentially expanded the surface area for cyberattacks. Besides significantly increasing the value of information stored on network systems around the world, cyber dependency grows with increasing digital interconnection among people, things, and organizations. As technology develops and pervades across industry sectors, the associated vulnerabilities will also become more pronounced.
For example, these emerging technologies can enable both the amassing and transmitting of big data and financial information, making the industries that adopt these new technologies attractive targets for cyberattacks. Further, the widespread use of mobile devices and IoT in daily business transactions can also lead to an exponential increase in the number of vulnerable entry points for potential attacks.
What Does This Mean for APAC?
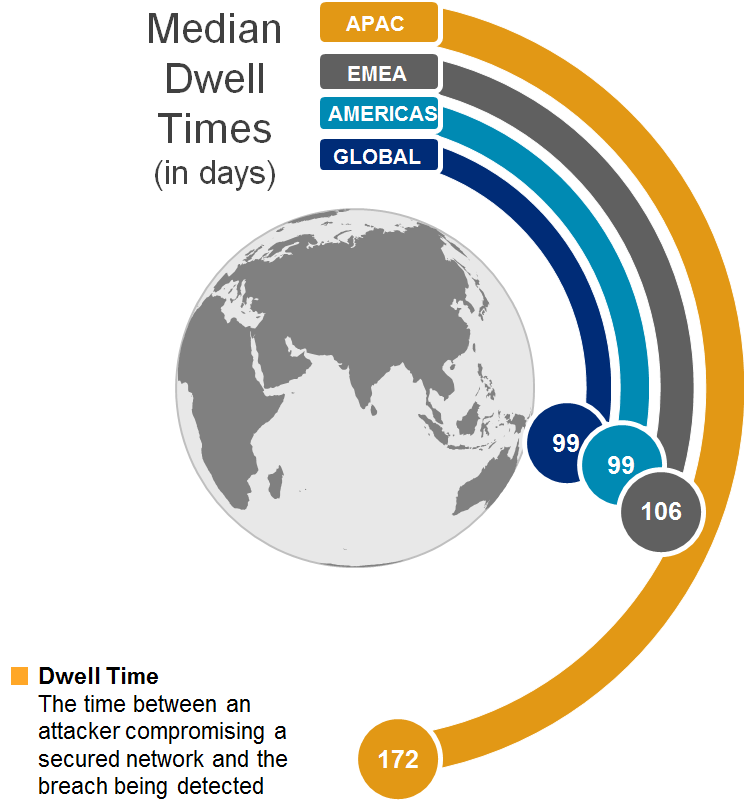
The APAC region is heterogeneous, and different economies differ widely in terms of their cybersecurity commitment and preparedness. According to FireEye, the median dwell time—the time between an attack and its detection—was 172 days in 2017 for APAC, significantly higher than the global average of 99 days. The high dwell time in APAC can be attributed to the lack of investment in cybersecurity measures, such as security awareness of workforce or capabilities for detecting cyberattacks.
Exhibit 2: The Asia-Pacific region continues to report the world’s highest dwell times
Key Drivers of Cyber Defense Challenges in APAC
Cyber risk has historically been among the top five risks for executives doing business in East Asia and the Pacific, but the various high-profile cyberattacks in 2017 have prompted them to pay closer attention to the potential damage of these attacks. The most notable is the WannaCry ransomware attack in May 2017 that severely disrupted businesses in major Asian economies, with China, India and Vietnam among the 20 countries hit hardest globally.
Having a cybersecurity landscape that is less mature than other regions, the APAC region appears to be more susceptible to cyberattacks. Hence, it must recognize and address several cybersecurity hurdles to improve its cyber defenses:
Geopolitical tensions create conflicts and uncertainties. APAC is home to numerous geopolitical hotspots. These create uncertainties for governments that, in turn, drive demand for confidential information, which fuels cyber espionage and the rush to gather intelligence information. Cyber espionage operations are mostly aimed at collecting information to understand adversaries’ tactics and capabilities and to identify key decision-makers. While government agencies are common targets, private sector organizations will also need to stay vigilant.
Exposed critical information infrastructure remains key target for adversaries. In recent years, potential cyberattacks against critical information infrastructure (CII) systems have become an important part of national security agendas. In particular, CII systems that manage utility plants, transportation networks, hospitals and other essential services remain vulnerable to the increasingly frequent and targeted attacks. Successful cyberattacks can adversely affect CII systems and disrupt essential services, in turn hurting businesses and consumer confidence levels and eventually impacting economic growth.
Cyber talent shortage. While worldwide spending on cyber defense products and services is forecast to reach as much as $1 trillion from 2017 to 2021, the lack of human capital to drive these cyber defense initiatives is another key roadblock. The global cybersecurity workforce is projected to face a serious shortage. As cyber risks become increasingly prevalent, companies must either find new recruitment channels or raise and enhance awareness of cybersecurity among existing IT employees. For example, companies such as Mandiant are working with several government and private enterprises to develop in-house cybersecurity capabilities.
What’s Next for 2018?
Companies need to seriously consider investing time and resources in their cybersecurity systems to keep pace with today’s evolving threat landscape. That first requires a comprehensive assessment of their current cybersecurity maturity by understanding their business infrastructure and identifying threat vectors that pose a risk to daily operations.
Recent cyber incidents have also become increasingly sophisticated, and it is evident that companies need to invest in capability-building by conducting scenario analyses, assuming data breach in preparation for any possible outcome and raising the awareness levels regarding breach response within organizations.
Finally, as demonstrated by the 2017 ransomware incidents, resuming operations after an attack is not as easy as switching the network back on. As soon as a breach occurs, companies may find themselves in an extended period of outage while network forensics experts determine the extent of the damage. Minimizing business disruption has often been overlooked by businesses, leading to unnecessary financial losses due to business interruption and operational inefficiencies. With appropriate resources allocated to critical areas for effective business continuity plans, the path to recovery should be smoother.
A mindset shift is critical for understanding the potential costs and loss of income caused by a potential cyber incident. From having a communications strategy in place to an incident response business continuity plan, tomorrow’s cyber landscape will pose an enterprise risk that goes far beyond what we have seen in 2017. The sooner governments and businesses recognize this, the better prepared we can all be for what is to come.